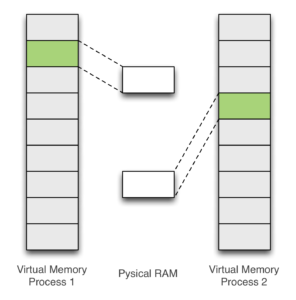
Tor'sHammer Attack on 192.168.1.9 IP with 5001 port number (see online... | Download Scientific Diagram

Atomic Tourism and False Memories: Cai Guo-Qiang's The Century with Mushroom Clouds – Tate Papers | Tate

Amazon.com: LOOYAR 32" PU Foam Medieval Crusader Battle Hammer Festival Props for Knight Warrior Costume Battle Play Halloween Cosplay LARP Silver : Clothing, Shoes & Jewelry
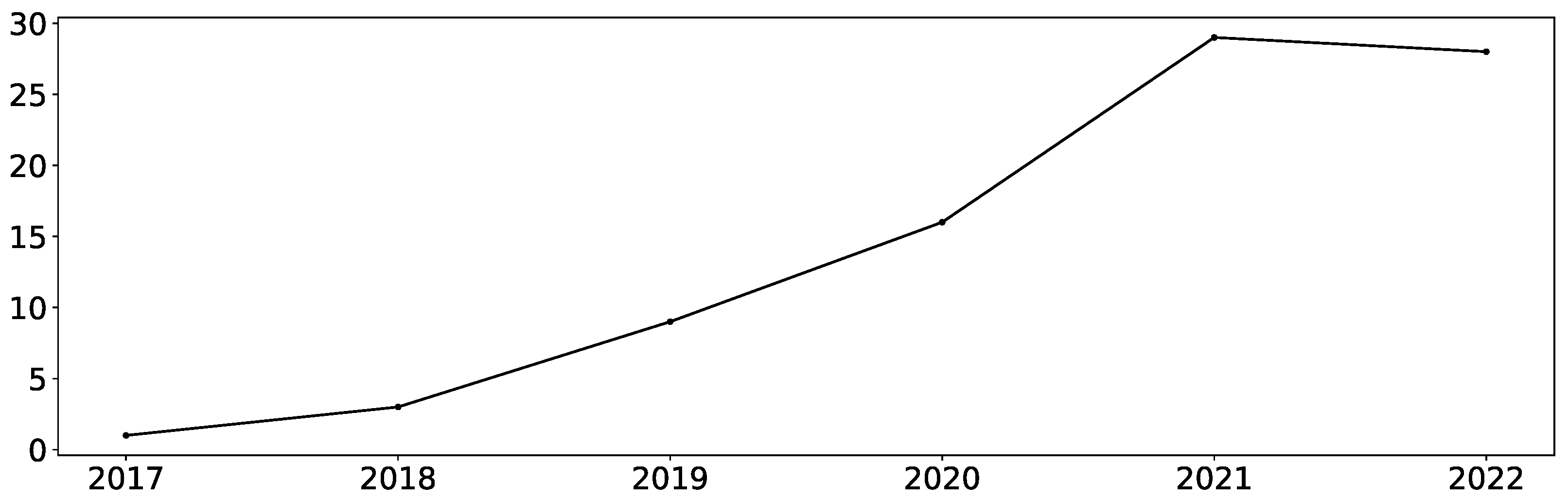
Electronics | Free Full-Text | A Survey of Bit-Flip Attacks on Deep Neural Network and Corresponding Defense Methods